绑定壳和反向壳的区别
shell 是一个程序,它解释我们的命令并将写入的命令提供给操作系统。它充当用户和操作系统之间的接口。它从键盘获取输入并将其提供给操作系统,终端允许您键入命令并与 shell 交互。
一些流行的外壳:
- Windows PowerShell
- Windows 命令提示符
- 重击
- 嘘
- 短跑
- 出生
- 科恩
港口
简而言之,端口是可以建立连接的开口。
例如,访问 https://geeksforgeeks.org 之类的网站,将建立到 443 端口的连接,因为 HTTPS 和服务器使用 443 端口进行连接。端口是与 IP 地址关联的数字。
一些常用的端口是:
- 端口 20 – FTP
- 端口 22 – SSH
- 端口 25 – SMTP
- 端口 80 - HTTP
- 端口 443 – HTTPS
- 端口 465 – SMTPS
- 端口 587 – SMTP
- 端口 993 – IMAP
绑定外壳:

绑定外壳
绑定外壳是一种设置,其中远程控制台通过网络与其他计算机建立。在 Bind shell 中,攻击者在目标计算机上启动服务,攻击者可以连接到该服务。在绑定外壳中,攻击者可以连接到目标计算机并在目标计算机上执行命令。要启动绑定 shell,攻击者必须拥有受害者的 IP 地址才能访问目标计算机。
反壳:
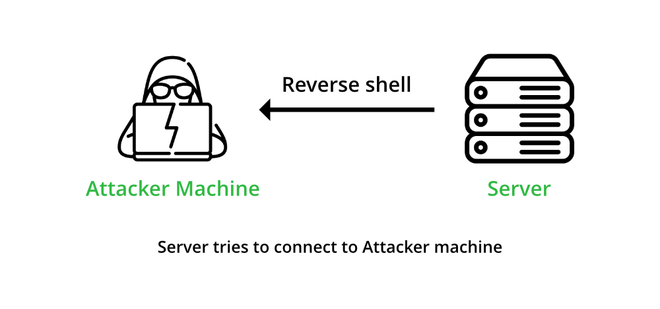
反向壳
反向外壳或回连是一种设置,攻击者必须首先在他的机器上启动服务器,而目标机器必须充当连接到攻击者服务的服务器的客户端。连接成功后,攻击者可以访问目标计算机的shell。
要启动反向 shell,攻击者无需知道受害者的 IP 地址即可访问目标计算机。
绑定壳和反向壳的区别
| S.NO. | Bind Shell | Reverse Shell |
|---|---|---|
| 1. | Bind Shells have the listener running on the target and the attacker connects to the listener in order to gain remote access to the target system. | In the reverse shell, the attacker has the listener running on his/her machine and the target connects to the attacker with a shell. So that attacker can access the target system. |
| 2. | In Bind shell, the attacker finds an open port on the server/ target machine and then tries to bind his shell to that port. | In the reverse shell, the attacker opens his own port. So that victim can connect to that port for successful connection. |
| 3. | The attacker must know the IP address of the victim before launching the Bind Shell. | The attacker doesn’t need to know the IP address of the victim, because the attacker is going to connect to our open port. |
| 4. | In Bind shell, the listener is ON on the target machine and the attacker connects to it. | The Reverse shell is opposite of the Bind Shell, in the reverse shell, the listener is ON on the Attacker machine and the target machine connects to it. |
| 5. | Bind Shell sometimes will fail, because modern firewalls don’t allow outsiders to connect to open ports. | Reverse Shell can bypass the firewall issues because this target machine tries to connect to the attacker, so the firewall doesn’t bother checking packets. |